Kerberos for Red Teamers
Lab Infrastructure Diagram
Basics of Kerberos
Kerberos is a stateless authentication protocol based on tickets. Kerberos is a protocol that allows users to authenticate on the network and access services and uses port 88 by default and has been the default authentication protocol for domain.
Kerberos allows users to authenticate against services without sending their passwords over the network. This is an great security measure to protect against attacks such as man-in-the-middle
Kerberos Authentication Process in depth
- TGT request: Authentication Service (AS)
- TGS request: Ticket-Granting Service (TGS)
- Service request: Application Request (AP)
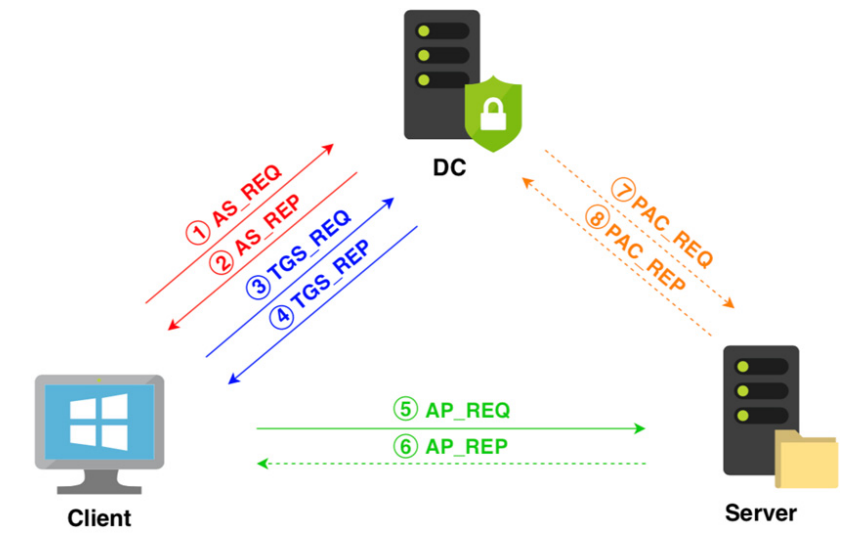
TGT - Request (AS-REQ)
First user sends TGT request or also called AS-REQ. To prove his validity the user needs to send a current timestamp which is encrypted with his key and also needs to be sent the Username in plaintext so the KDC can know whom it is dealing with.
TGT - Response (AS-REP)
TGS - Request (TGS-REQ)
TGS - Response (TGS-REP)
TGS - Response (AP-REQ)
TGS - Response (AP-REP)
How Tickets are Protected ?
- TGT The TGT sent by the KDC to the user is encrypted using the secret key of the KDC (KRBTGT account hash), which is known only from the KDC.
- TGS The TGS ticket sent by the KDC to the user is encrypted using the service’s secret key.
Kerberos Attacks Basic Overview
Kerberoasting
Kerberoasting is a post-exploitation technique that obtains a hash of an Active Directory account that has a Service Principal Name (SPN). Every authenticated domain user can request a Kerberos ticket for an SPN. The retrieved Keberos ticket is encrypted with the hash of the service account which is associated with the requested SPN.
More in depth Explanation and Demo of the attack in this Blog Post
AS-REP Roasting
AS-REP roasting is a technique that allows retrieving TGT (AS-REP) for users that have “Do not require Kerberos preauthentication” property selected. Attacker is able to crack the part that of the received TGT (AS-REP) that is encrypted with user’s hash with tool such as John The Ripper or HashCat
More in depth Explanation and Demo of the attack in this Blog Post
Skeleton Key
The Skeleton Key attack is malware that can be injected into the LSASS process on a Domain Controller. This gives the Attacker opportunity to log in with any user in the Active Directory.
NOTE:
- It should not be used in real life engagement unless it’s given permission to be performed this attack (Because the security of the whole Active Directory is going to be downgraded’)
Silver Ticket
Silver ticket is attack that creates valid TGS ticket once the hash of the service account (Machine account or User account) is compromised which gives the attacker opportunity to choose what information to put into the TGS ticket in order to access the service.
More in depth Explanation and Demo of the attack in this Blog Post
Golden Ticket
The attack assumes compromising of KRBTGT account which will be used for forging a valid TGT as any user in the Active Directory and use the privileges of the user to access other services or resources
More in depth Explanation and Demo of the attack in this Blog Post
Diamond Ticket
Almost the same as golden ticket just with the difference that valid TGT is forged and with the help of the compromised hash of the account KRBTGT the forged TGT is decrypted and modified.
More in depth Explanation and Demo of the attack in this Blog Post
Pass the Hash (PtH)
Pass the hash is a technique that allows you to authenticate to a Windows service using NTLM hash of the user. Technique works by starting a new logon session with a fake identity and then replacing the session information with the domain, username, and NTLM hash provided during the login process.
More in depth Explanation and Demo of the attack in this Blog Post
Pass the Ticket (PtT)
Pass the ticket is a technique that uses Kerberos authentication. TGT tickets could be retrieved from extracting LSASS process (High Level Privileges needed)
More in depth Explanation and Demo of the attack in this Blog Post
OverPass the Hash/Pass the Key (PtK)
Overpass the hash is a technique which you can request a Kerberos TGT for a user, using their NTLM or AES hash (OPSEC). No high level privileges required to forge ticket with user’s password hash, but to extract the hashes you will need high level privileges
More in depth Explanation and Demo of the attack in this Blog Post
Constrained Delegation
Constrained delegation allows the account with the “Trust this user/computer for delegation to specified services only” enabled to impersonate ANY user to access specific services.
Kerberos has two of extensions for this type of delegation:
- Service for User to Self (S4U2Self) — Kerberos protocol transition extension.
- Service for User to Proxy (S4U2Proxy) — Kerberos Constrained Delegation extension.
More in depth Explanation and Demo of the attack in this Blog Post
Unconstrained Delegation
- Computers:
- If we are able to compromise a server that has unconstrained delegation enabled and a Domain Admin or any other User logs in we will be able to extract their TGT
- Users:
- If we are able to compromise a user which is configured with Unconstrained Delegation we are able to get the TGT of the Domain Controller combined with Printer Bug.
Unconstrained delegation is enabled by default and required on all Domain Controllers (DCs)
Configuring Unconstrained Delegation by setting the TRUSTED_FOR_DELEGATION flag to true in the userAccountControl attribute of the user running the service that will make use of delegation.
More in depth Explanation and Demo of the attack in this Blog Post
Resource-Based Constrained Delegation (RBCD)
To be able to abuse RBCD we need user with enough privileges to modify msDS-AllowedToActOnBehalfOfOtherIdentity property on a computer and the second we need to have control over another object that has an SPN like a user account having a ServicePrincipalName set.
More in depth Explanation and Demo of the attack in this Blog Post
SID-History Injection
SID History is designed to support migration scenarios of a user from one domain to another and have again his access to the resources into the old domain, the user’s previous SID is added to the SID History of their account.
Attack is combined with either Golden or Diamond Ticket Attack. So when creating such a ticket, the SID of privileged groups such as (EAs, DAs, etc) can be added into the SID History property of the user and the user will have access to all resources in the parent.
More in depth Explanation and Demo of the attack in this Blog Post
DCSync
DCSync attack simulates the behavior of a Domain Controller and can ask other Domain Controllers (DCs) to replicate information. This attack uses Directory Replication Service Remote Protocol (MS-DRSR) the protocol is highly important for the proper functionality of the Active Directory and cannot be turned of. To perform DCSync attack we high level privileged account or to have these 3 rights on the Domain Object:
- Replicating Directory Changes (DS-Replication-Get-Changes)
- Replicating Directory Changes All (DS-Replication-Get-Changes-All)
- Replicating Directory Changes In Filtered Set (DS-Replication-Get-Changes-In-Filtered-Set)
More in depth Explanation and Demo of the attack in this Blog Post
